菜到哭泣。
reverse
Easy Android

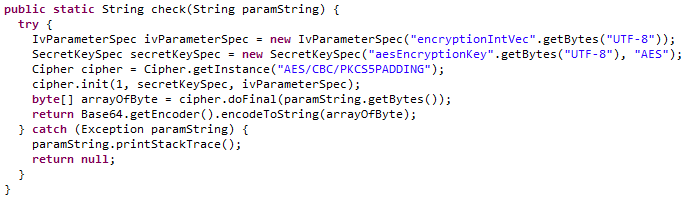
参数都在上面的函数里有(数据块128位没找到,我猜的)。
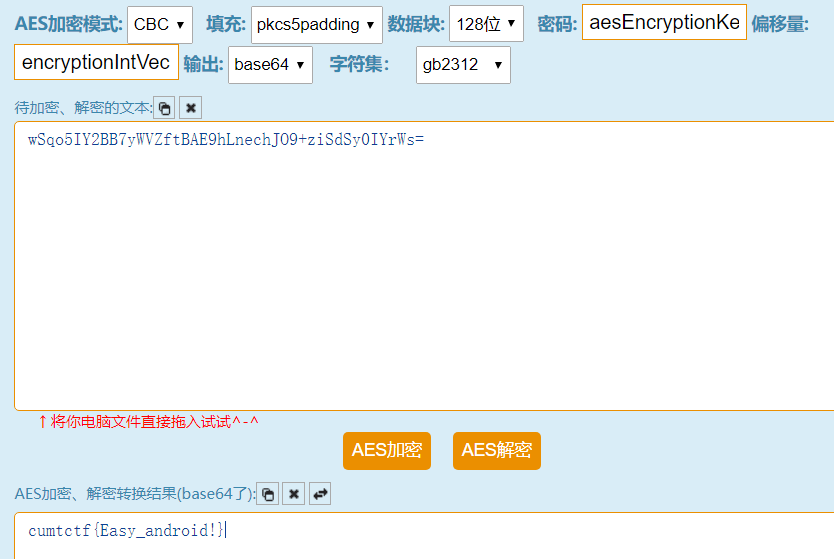
Medium Android
变种base64.
主函数:
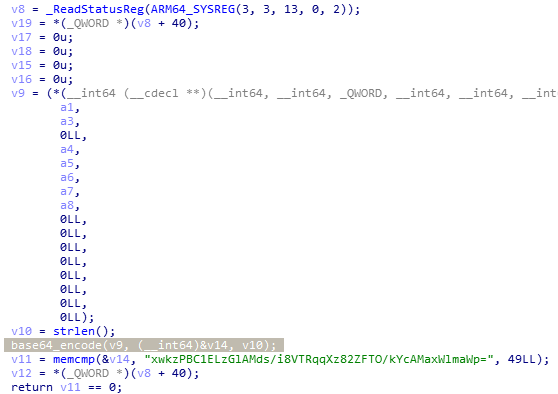
base64_encode:
下图代码将字符串nF67gMB4w50pQCiHVRzDTU3ZL28lcPmKyqesAOExWokXb9h+dNIj1SuaJ/rYvtGf反转并作为base64的码表。
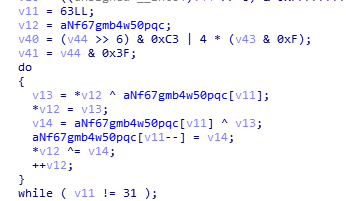
1 | //反转字符串 |
错误脚本
一开始误以为算法就是换了码表的base64,写出下面的脚本:
1 | import base64 |
str1是密文,string1为新码表,string2为默认码表。
输出b'cum\x8b\x9c\x8bf{A\x91\xbe\x8fple\xbe\xbb\x9eyKe\x9a\x8f\xabheD\x8d\xbe\x88ay!!}'
或者可以用下面的脚本:
1 | base64_charset = 'nF67gMB4w50pQCiHVRzDTU3ZL28lcPmKyqesAOExWokXb9h+dNIj1SuaJ/rYvtGf'[::-1] |
输出cum***f{A***ple***yKe***heD***ay!!} (非法字符用*代替)
正确脚本
观察上面的字符串,三个正常,三个非法,并且最重要的,第一处非法的三个字符一定是tct(因为cumtctf),观察二进制10001011 10011100 10001011,一三的二进制相同,按位反转后,10001011是01110100,恰好是字符t.
所以猜测算法不仅是换了码表的base64,而且奇数的每三个字符(看不懂的话对照一下上面字符串的*星号的位置,数学表达就是6k+3,6k+4,6k+5, k=1,2,3,4,5)都要按位翻转。
1 | base64_charset = 'nF67gMB4w50pQCiHVRzDTU3ZL28lcPmKyqesAOExWokXb9h+dNIj1SuaJ/rYvtGf'[::-1] |
按位翻转其实就是按位与1异或,对于8位二进制而言,就是与0b11111111即0xff异或
输出cumtctf{AnAppleADayKeepTheDrAway!**
综合上面的cum***f{A***ple***yKe***heD***ay!!}
flag就是cumtctf{AnAppleADayKeepTheDrAway!!}
easy_vm
主函数
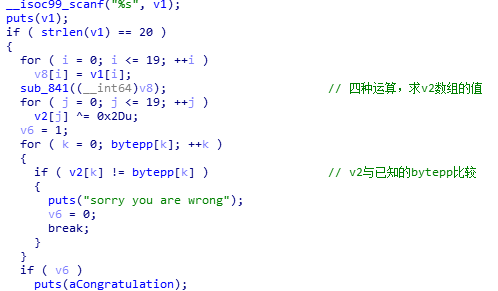
加密函数
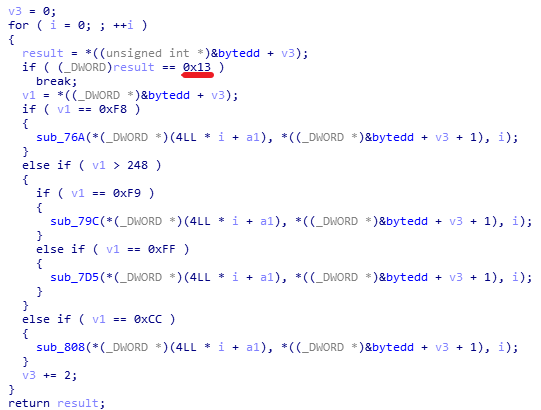
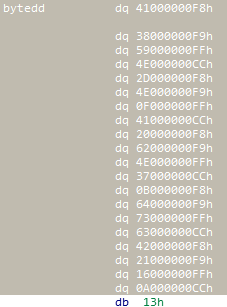
bytedd:
第一个字节是数据,第四个字节是操作码,4个操作码对应4种运算。
最后的13h是结束循环的标志,请对照上上图中的红线处。
1 | bytepp = [0xa, 0xa1,0x5d,0x56,0x7b,0xab,0x57,0x77,0x3c,0x5e,0x64,0xe1,0x49,0xb2,0x60,0x6f,0x1,0x5d,0x8a,0x148,0x50] |
四种运算,分别逆向算法。逻辑很简单,所以这里就不详细分析了。
PWN
eeeeeeasy
主函数:
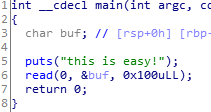
并且发现了调用system("/bin/sh")的函数。
1 | from pwn import * |
但是写wp时,不知道为什么本地没打通,搞不明白。
0x4005b6是system('/bin/sh')的地址。
what is shellcode?
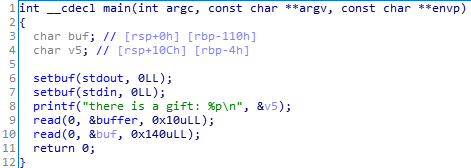
通过第八行输出的v5的地址,计算出buf的地址。
第一个read没用,随便写点数据。
第二个read,写入shellcode,并填充垃圾字符,直至ret处。返回地址为buf的地址(即shellcode的地址)
1 | from pwn import * |
CRYPTO
仿射密码
密文:cejldputgtbjwrfhpttnt
穷举即可,从几百条字符串中找到flag
参考:【密码学】古典密码
1 | #-*- coding:utf-8 -*- |
MISC
你可劲找之word
打开word,发现flag,但是禁止复制,所以手打即可。
你可劲找之JPG
winhex打开,文件末尾有flag
你可劲找之音乐贼好听
二维码修复,得到key:BxS1909
然后使用MP3Stego从mp3中分出flag
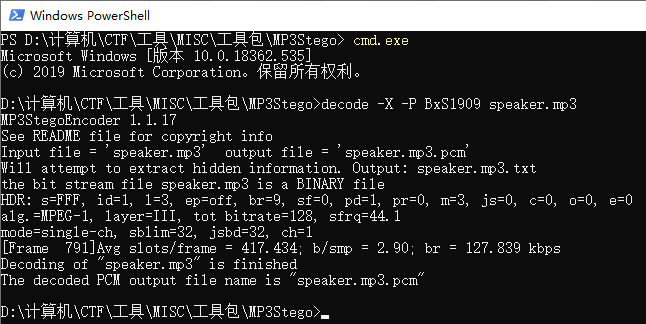
flag在目录下的speaker.mp3.txt内。