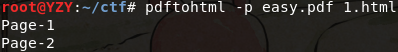
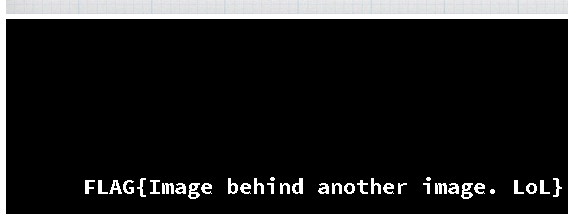
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
| root@kali:~/tool# ./pkcrack-install.sh
./pkcrack-install.sh: line 1: !/bin/bash: No such file or directory
--2019-10-25 22:37:33-- https://www.unix-ag.uni-kl.de/~conrad/krypto/pkcrack/pkcrack-1.2.2.tar.gz
Resolving www.unix-ag.uni-kl.de (www.unix-ag.uni-kl.de)... 131.246.124.83, 2001:638:208:ef34:0:ff:fe00:83
Connecting to www.unix-ag.uni-kl.de (www.unix-ag.uni-kl.de)|131.246.124.83|:443... connected.
HTTP request sent, awaiting response... 200 OK
Length: 174208 (170K) [application/x-gzip]
Saving to: ‘pkcrack-1.2.2.tar.gz’
pkcrack-1.2.2.tar.g 100%[===================>] 170.12K 3.04KB/s in 56s
2019-10-25 22:38:31 (3.04 KB/s) - ‘pkcrack-1.2.2.tar.gz’ saved [174208/174208]
gcc -O6 -Wall -c -o crc.o crc.c
crc.c:24:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: crc.c,v 1.3 1997/09/18 18:07:24 lucifer Release1_2_1 $";
^~~~~
gcc -O6 -Wall -c -o mktmptbl.o mktmptbl.c
mktmptbl.c: In function ‘preCompTemp’:
mktmptbl.c:58:5: warning: implicit declaration of function ‘memset’ [-Wimplicit-function-declaration]
memset(numEntries, 0, sizeof(numEntries));
^~~~~~
mktmptbl.c:58:5: warning: incompatible implicit declaration of built-in function ‘memset’
mktmptbl.c:58:5: note: include ‘<string.h>’ or provide a declaration of ‘memset’
mktmptbl.c:47:1:
+#include <string.h>
mktmptbl.c:58:5:
memset(numEntries, 0, sizeof(numEntries));
^~~~~~
mktmptbl.c: In function ‘initMulTab’:
mktmptbl.c:93:5: warning: incompatible implicit declaration of built-in function ‘memset’
memset(mTab2Counter, 0, sizeof(mTab2Counter));
^~~~~~
mktmptbl.c:93:5: note: include ‘<string.h>’ or provide a declaration of ‘memset’
At top level:
mktmptbl.c:43:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: mktmptbl.c,v 1.9 2002/11/02 15:12:06 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o main.o main.c
main.c:131:6: warning: return type of ‘main’ is not ‘int’ [-Wmain]
void main( int argc, char **argv )
^~~~
main.c:70:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: main.c,v 1.15 2002/11/12 16:58:02 lucifer Exp $";
^~~~~
main.c: In function ‘main’:
main.c:265:2: warning: ‘plain’ may be used uninitialized in this function [-Wmaybe-uninitialized]
close( plain );
^~~~~~~~~~~~~~
main.c:267:2: warning: ‘crypt’ may be used uninitialized in this function [-Wmaybe-uninitialized]
close( crypt );
^~~~~~~~~~~~~~
gcc -O6 -Wall -c -o stage1.o stage1.c
stage1.c:41:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: stage1.c,v 1.8 2002/01/31 16:27:08 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o keystuff.o keystuff.c
keystuff.c:32:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: keystuff.c,v 1.5 2002/11/02 15:12:06 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o stage2.o stage2.c
stage2.c:56:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: stage2.c,v 1.16 2003/01/03 15:18:18 lucifer Exp $";
^~~~~
stage2.c: In function ‘recursion2’:
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c: In function ‘buildKey2Lists’:
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
stage2.c:293:33: warning: ‘oldValue’ may be used uninitialized in this function [-Wmaybe-uninitialized]
if( !hadIt || oldValue != newKey )
~~~~~~~~~^~~~~~~~~
stage2.c:263:48: note: ‘oldValue’ was declared here
uword key2j, key2iminus1, key2iminus2, newKey, oldValue;
^~~~~~~~
gcc -O6 -Wall -c -o stage3.o stage3.c
stage3.c:51:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: stage3.c,v 1.10 2002/12/30 18:27:25 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o exfunc.o exfunc.c
exfunc.c:48:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: exfunc.c,v 1.9 2003/01/05 14:40:37 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o readhead.o readhead.c
readhead.c: In function ‘read_local’:
readhead.c:318:21: warning: unused variable ‘sig’ [-Wunused-variable]
unsigned long sig;
^~~
At top level:
readhead.c:71:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: readhead.c,v 1.13 2003/01/05 14:40:37 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o writehead.o writehead.c
writehead.c: In function ‘write_sig’:
writehead.c:64:52: warning: format ‘%lx’ expects argument of type ‘long unsigned int’, but argument 3 has type ‘int’ [-Wformat=]
fprintf( stderr, "Write unknown signature: 0x%08lx\n", sigType );
~~~~^ ~~~~~~~
%08x
At top level:
writehead.c:33:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: writehead.c,v 1.4 2003/01/05 14:40:37 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o zipdecrypt.o zipdecrypt.c
zipdecrypt.c: In function ‘zipdecrypt’:
zipdecrypt.c:244:47: warning: comparison of constant ‘0’ with boolean expression is always false [-Wbool-compare]
err = (!read_ddesc(infile, 0) < 0);
^
zipdecrypt.c:244:47: warning: logical not is only applied to the left hand side of comparison [-Wlogical-not-parentheses]
zipdecrypt.c:244:24: note: add parentheses around left hand side expression to silence this warning
err = (!read_ddesc(infile, 0) < 0);
^~~~~~~~~~~~~~~~~~~~~~
( )
At top level:
zipdecrypt.c:76:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: zipdecrypt.c,v 1.16 2003/01/05 14:40:37 lucifer Exp $";
^~~~~
gcc -O6 -Wall -c -o debug.o debug.c
debug.c:17:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: debug.c,v 1.2 2002/01/30 15:25:26 lucifer Exp $";
^~~~~
gcc -o pkcrack -O6 -Wall crc.o mktmptbl.o main.o stage1.o keystuff.o stage2.o stage3.o exfunc.o readhead.o writehead.o zipdecrypt.o debug.o
gcc -O6 -Wall -c -o zdmain.o zdmain.c
zdmain.c:38:6: warning: return type of ‘main’ is not ‘int’ [-Wmain]
void main( int argc, char **argv )
^~~~
zdmain.c:28:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: zdmain.c,v 1.4 2002/12/28 17:01:42 lucifer Exp $";
^~~~~
gcc -o zipdecrypt -O6 -Wall zdmain.o zipdecrypt.o crc.o keystuff.o writehead.o readhead.o
gcc -O6 -Wall -c -o findkey.o findkey.c
findkey.c:59:6: warning: return type of ‘main’ is not ‘int’ [-Wmain]
void main( int argc, char **argv )
^~~~
findkey.c:48:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: findkey.c,v 1.6 2002/11/02 15:12:06 lucifer Exp $";
^~~~~
gcc -o findkey -O6 -Wall findkey.o crc.o stage3.o keystuff.o mktmptbl.o
gcc -O6 -Wall -c -o extract.o extract.c
extract.c:93:6: warning: return type of ‘main’ is not ‘int’ [-Wmain]
void main(int argc, char *argv[])
^~~~
extract.c:76:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: extract.c,v 1.12 2002/12/28 16:09:59 lucifer Exp $";
^~~~~
gcc -o extract -O6 -Wall extract.o exfunc.o readhead.o
gcc -O6 -Wall -c -o makekey.o makekey.c
makekey.c: In function ‘usage’:
makekey.c:24:5: warning: implicit declaration of function ‘exit’ [-Wimplicit-function-declaration]
exit( 1 );
^~~~
makekey.c:24:5: warning: incompatible implicit declaration of built-in function ‘exit’
makekey.c:24:5: note: include ‘<stdlib.h>’ or provide a declaration of ‘exit’
makekey.c:18:1:
+#include <stdlib.h>
makekey.c:24:5:
exit( 1 );
^~~~
makekey.c: At top level:
makekey.c:27:6: warning: return type of ‘main’ is not ‘int’ [-Wmain]
void main( int argc, char **argv )
^~~~
makekey.c:19:13: warning: ‘RCSID’ defined but not used [-Wunused-variable]
static char RCSID[]="$Id: makekey.c,v 1.1 1997/02/15 09:44:44 lucifer Release1_2_1 $";
^~~~~
gcc -o makekey -O6 -Wall makekey.o crc.o keystuff.o
|