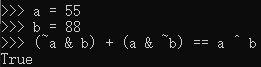1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
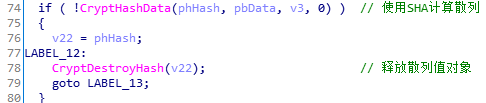
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
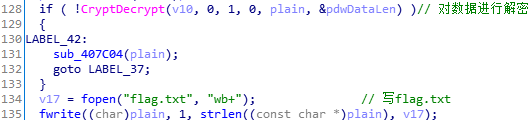
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
177
178
179
180
181
182
183
184
185
186
187
188
189
190
191
192
193
194
195
196
197
198
199
200
201
202
203
204
205
206
207
208
209
210
211
212
213
214
215
216
217
218
219
220
221
222
223
224
225
226
227
228
229
230
231
232
233
234
235
236
237
238
239
240
241
242
243
244
245
246
247
248
249
250
251
252
253
254
255
256
257
258
259
260
261
262
263
264
265
266
267
268
269
270
271
272
273
274
275
276
277
278
279
280
281
282
283
284
285
286
287
288
289
290
291
292
293
294
295
296
297
298
299
300
301
302
303
304
305
306
307
308
309
310
311
312
313
314
315
316
317
318
319
320
321
322
323
324
325
326
327
328
329
330
331
332
333
334
335
336
337
338
339
340
341
342
343
344
345
346
347
348
349
350
351
352
353
354
355
356
357
358
359
360
361
362
363
364
365
366
367
368
369
370
371
372
373
374
375
376
377
378
379
380
381
382
383
384
385
386
387
388
389
390
391
392
393
394
395
396
397
398
399
400
401
402
403
404
405
406
407
408
409
410
411
412
413
414
415
416
417
418
419
420
421
422
423
424
425
426
427
428
429
430
431
432
433
434
435
436
437
438
439
440
441
442
443
444
445
446
447
448
449
450
451
452
453
454
455
456
457
458
459
460
461
462
463
464
465
466
467
468
469
470
471
472
473
474
475
476
| Registers:
R0 x0000 0
R1 x0000 0
R2 x0000 0
R3 x0000 0
R4 x0000 0
R5 x0000 0
R6 x0000 0
R7 x0000 0
PC x3000 12288
IR x0000 0
CC Z
Memory:
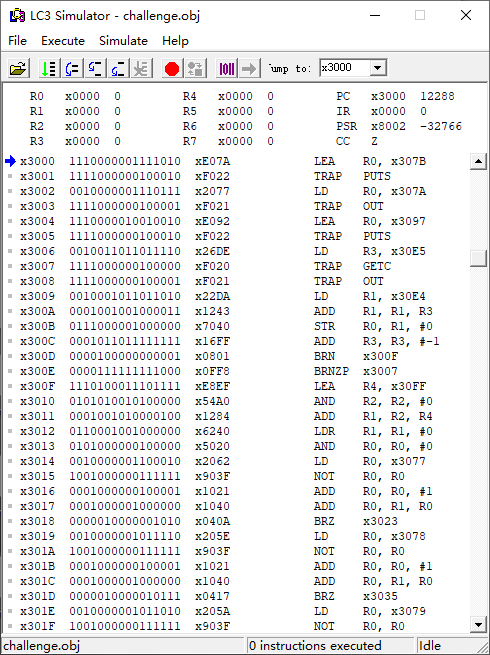
x3000 1110000001111010 xE07A LEA R0, x307B ;WELCOME TO WORLD OF LC3
x3001 1111000000100010 xF022 TRAP PUTS
x3002 0010000001110111 x2077 LD R0, x307A ;0x0A,换行
x3003 1111000000100001 xF021 TRAP OUT
x3004 1110000010010010 xE092 LEA R0, x3097 ;PLEASE INPUT YOUR FLAG:
x3005 1111000000100010 xF022 TRAP PUTS
x3006 0010011011011110 x26DE LD R3, x30E5 ;R3 = [0x30E5] = 0x18 ;flag长度
x3007 1111000000100000 xF020 TRAP GETC ;从缓冲区接收一个字符
x3008 1111000000100001 xF021 TRAP OUT ;输出这个字符
x3009 0010001011011010 x22DA LD R1, x30E4 ;R1 = [0x30E4] = 0x4000
x300A 0001001001000011 x1243 ADD R1, R1, R3 ;R1 = R1 + R3
x300B 0111000001000000 x7040 STR R0, R1, #0 ;[R1 + 0] = R0 ;[0x4000] = R0,字符串存储在0x4000
x300C 0001011011111111 x16FF ADD R3, R3, #-1 ;R3 = R3 - 1 ;所以输入后的字符串的存储是倒序的
x300D 0000100000000001 x0801 BRN x300F
x300E 0000111111111000 x0FF8 BRNZP x3007
x300F 1110100011101111 xE8EF LEA R4, x30FF ;R4 = 0x30FF
x3010 0101010010100000 x54A0 AND R2, R2, #0 ;R2 = 0
x3011 0001001010000100 x1284 ADD R1, R2, R4 ;R1 = 0x30FF + R2
x3012 0110001001000000 x6240 LDR R1, R1, #0 ;R1 = [R1] = [0x30FF + R2]
x3013 0101000000100000 x5020 AND R0, R0, #0 ;R0 = 0
x3014 0010000001100010 x2062 LD R0, x3077 ;R0 = [0x3077]
x3015 1001000000111111 x903F NOT R0, R0 ;R0 = ~R0 = ~[0X3077]
x3016 0001000000100001 x1021 ADD R0, R0, #1 ;R0 = ~[0X3077] + 1
x3017 0001000001000000 x1040 ADD R0, R1, R0 ;R0 = [0x30FF + R2] + (~[0x3077] + 1) = [0x30FF + R2] - [0x3077]
x3018 0000010000001010 x040A BRZ x3023 ;意思是若R0等于0([0x30FF + R2] == [0x3077] = 0x11),则一直跳转到0x3023
x3019 0010000001011110 x205E LD R0, x3078
x301A 1001000000111111 x903F NOT R0, R0
x301B 0001000000100001 x1021 ADD R0, R0, #1
x301C 0001000001000000 x1040 ADD R0, R1, R0
x301D 0000010000010111 x0417 BRZ x3035 ;[0x30FF + R2] == [0x3078] = 0x13
x301E 0010000001011010 x205A LD R0, x3079
x301F 1001000000111111 x903F NOT R0, R0
x3020 0001000000100001 x1021 ADD R0, R0, #1
x3021 0001000001000000 x1040 ADD R0, R1, R0
x3022 0000010000100101 x0425 BRZ x3048 ;[0x30FF + R2] == [0x3079] = 0x14
x3023 0001001010100001 x12A1 ADD R1, R2, #1 ;R1 = R2 + 1
x3024 0001001100000001 x1301 ADD R1, R4, R1 ;R1 = R4 + R2 + 1 ;R4 = 0x30FF
x3025 0110001001000000 x6240 LDR R1, R1, #0 ;R1 = [R4 + R2 + 1]
x3026 0001110001100000 x1C60 ADD R6, R1, #0 ;R6 = R1
x3027 0001001010100010 x12A2 ADD R1, R2, #2 ;R1 = R2 + 2
x3028 0001001100000001 x1301 ADD R1, R4, R1 ;R1 = R4 + (R2 + 2)
x3029 0110001001000000 x6240 LDR R1, R1, #0 ;R1 = [R4 + R2 + 2]
x302A 0010000010111001 x20B9 LD R0, x30E4 ;R0 = [0x30E4] ;flag基址0x4000
x302B 0001000001100000 x1060 ADD R0, R1, #0 ;R0 = [0x30E4] + [R4 + R2 + 2]
x302C 0110000000000000 x6000 LDR R0, R0, #0 ;R0 = [[0x30E4] + [R4 + R2 + 2]] = flag[[0x30FF + R2 + 2]]
x302D 0001111000100000 x1E20 ADD R7, R0, #0 ;R7 = flag[[0x30FF + R2 + 2]]
x302E 0001101001100000 x1A60 ADD R5, R1, #0 ;R5 = [0x30FF + R2 + 2]
x302F 0000111000101001 x0E29 BRNZP x3059
x3030 0010001010110011 x22B3 LD R1, x30E4 ;R1 = [0x30E4] = 0x4000
x3031 0001001101000001 x1341 ADD R1, R5, R1 ;R1 = 0x4000 + [0x30FF + R2 + 2]
x3032 0111000001000000 x7040 STR R0, R1, #0 ;[R1] = R0 ;flag[[0x30FF + R2 + 2]] = [0x30FF + R2 + 1] + flag[[0x30FF + R2 + 2]]
x3033 0001010010100011 x14A3 ADD R2, R2, #3 ;R2 += 3
x3034 0000111111011100 x0FDC BRNZP x3011
x3035 0001001010100001 x12A1 ADD R1, R2, #1 ;R1 = R2 + 1
x3036 0001001100000001 x1301 ADD R1, R4, R1 ;R1 = R4 + R2 + 1
x3037 0110001001000000 x6240 LDR R1, R1, #0 ;R1 = [R4 + R2 + 1]
x3038 0010000010101011 x20AB LD R0, x30E4 ;R0 = 0x4000
x3039 0001000000000001 x1001 ADD R0, R0, R1 ;R0 = 0X4000 + [R4 + R2 + 1]
x303A 0110110000000000 x6C00 LDR R6, R0, #0 ;R6 = [R0] = FLAG[[0x30FF + R2 + 1]]
x303B 0001001010100010 x12A2 ADD R1, R2, #2 ;R1 = R2 + 2
x303C 0001001100000001 x1301 ADD R1, R4, R1 ;R1 = R4 + R1 = R4 + R2 + 2
x303D 0110001001000000 x6240 LDR R1, R1, #0 ;R1 = [0x30FF + R2 + 2]
x303E 0010000010100101 x20A5 LD R0, x30E4 ;R0 = 0X4000
x303F 0001000000000001 x1001 ADD R0, R0, R1 ;R0 = 0X4000 + [0x30FF + R2 + 2]
x3040 0001101001100000 x1A60 ADD R5, R1, #0 ;R5 = [0x30FF + R2 + 2]
x3041 0110111000000000 x6E00 LDR R7, R0, #0 ;R7 = [0X4000 + [0x30FF + R2 + 2]] = FLAG[[0x30FF + R2 + 2]]
x3042 0000111000011000 x0E18 BRNZP x305B
x3043 0010001010100000 x22A0 LD R1, x30E4 ;R1 = 0X4000
x3044 0001001001000101 x1245 ADD R1, R1, R5 ;R1 = 0X4000 + [0x30FF + R2 + 2]
x3045 0111000001000000 x7040 STR R0, R1, #0 ;[R1] = R0 ;FLAG[[0x30FF + R2 + 2]] = ((FLAG[[0x30FF + R2 + 1]]) & (~(FLAG[[0x30FF + R2 + 2]]))) + ((~FLAG[[0x30FF + R2 + 1]]) & (FLAG[[0x30FF + R2 + 2]]))
x3046 0001010010100011 x14A3 ADD R2, R2, #3 ;R2 = R2 + 3
x3047 0000111111001001 x0FC9 BRNZP x3011
x3048 0001001010100001 x12A1 ADD R1, R2, #1 ;R1 = R2 + 1
x3049 0001001100000001 x1301 ADD R1, R4, R1 ;R1 = R4 + R2 + 1
x304A 0110001001000000 x6240 LDR R1, R1, #0 ;R1 = [R4 + R2 + 1]
x304B 0001110001100000 x1C60 ADD R6, R1, #0 ;R6 = R1 = [R4 + R2 + 1]
x304C 0001001010100010 x12A2 ADD R1, R2, #2 ;R1 = R2 + 2
x304D 0001001100000001 x1301 ADD R1, R4, R1 ;R1 = R4 + R2 + 2
x304E 0110001001000000 x6240 LDR R1, R1, #0 ;R1 = [R4 + R2 + 2]
x304F 0010101010010101 x2A95 LD R5, x30E5 ;R5 = 0x18
x3050 1001001001111111 x927F NOT R1, R1 ;R1 = ~R1 ;R1 = ~[R4 + R2 + 2]
x3051 0001001001100001 x1261 ADD R1, R1, #1 ;R1 = ~[R4 + R2 + 2] + 1
x3052 0001101101000001 x1B41 ADD R5, R5, R1 ;R5 = 0x18 + (~[R4 + R2 + 2] + 1) ;取非再加一的数学含义是取相反数,R5是用来标志循环是否结束的变量,初值0x18,终值为0.
x3053 0001111101100000 x1F60 ADD R7, R5, #0 ;R7 = R5 = 0x18 + (~[0x30FF + R2 + 2] + 1) ;考虑到[0x30FF + R2 + 2]的值为0x0~0x18,所以结果是0x18 - i,同时别忘了前面说过的字符串是倒序存储的
x3054 0000111000001100 x0E0C BRNZP x3061
x3055 0001101101100000 x1B60 ADD R5, R5, #0 ;if (R5 == 0) ????可能会影响标志位????
x3056 0000010000010101 x0415 BRZ x306C ;GOTO SUCCESS
x3057 0001010010100011 x14A3 ADD R2, R2, #3 ;R2 += 3
x3058 0000111110111000 x0FB8 BRNZP x3011
x3059 0001000110000111 x1187 ADD R0, R6, R7 ;R0 = [0x30FF + R2 + 1] + flag[[0x30FF + R2 + 2]]
x305A 0000111111010101 x0FD5 BRNZP x3030
x305B 1001000110111111 x91BF NOT R0, R6 ;R0 = ~R6 = ~FLAG[[0x30FF + R2 + 1]]
x305C 0101000000000111 x5007 AND R0, R0, R7 ;R0 = (~FLAG[[0x30FF + R2 + 1]]) & (FLAG[[0x30FF + R2 + 2]])
x305D 1001001111111111 x93FF NOT R1, R7 ;R1 = ~(FLAG[[0x30FF + R2 + 2]])
x305E 0101001110000001 x5381 AND R1, R6, R1 ;R1 = (FLAG[[0x30FF + R2 + 1]]) & (~(FLAG[[0x30FF + R2 + 2]]))
x305F 0001000001000000 x1040 ADD R0, R1, R0 ;R0 = ((FLAG[[0x30FF + R2 + 1]]) & (~(FLAG[[0x30FF + R2 + 2]]))) + ((~FLAG[[0x30FF + R2 + 1]]) & (FLAG[[0x30FF + R2 + 2]]))
x3060 0000111111100010 x0FE2 BRNZP x3043
x3061 0010000010000010 x2082 LD R0, x30E4 ;R0 = 0X4000
x3062 0001000000000110 x1006 ADD R0, R0, R6 ;R0 = 0X4000 + [0x30FF + R2 + 1]
x3063 0110000000000000 x6000 LDR R0, R0, #0 ;R0 = [0X4000 + [0x30FF + R2 + 1]] = FLAG[[0x30FF + R2 + 1]]
x3064 1110001010000001 xE281 LEA R1, x30E6 ;R1 = 0x30E6 ;这里是LEA,不是LDR,我个老花眼看错了,怪不得下一条指令不太对劲。
x3065 0001001001000111 x1247 ADD R1, R1, R7 ;R1 = 0x30E6 + 0x18 + (~[0x30FF + R2 + 2] + 1)
x3066 0110001001000000 x6240 LDR R1, R1, #0 ;R1 = [0x30E6 + 0x18 + (~[0x30FF + R2 + 2] + 1)]
x3067 1001001001111111 x927F NOT R1, R1 ;R1 = ~[0x30E6 + 0x18 + (~[0x30FF + R2 + 2] + 1)]
x3068 0001001001100001 x1261 ADD R1, R1, #1 ;R1 = ~[0x30E6 + 0x18 + (~[0x30FF + R2 + 2] + 1)] + 1 ;取[0x30E6 + 0x18 + (~[0x30FF + R2 + 2] + 1)]的相反数
x3069 0001000000000001 x1001 ADD R0, R0, R1 ;R0 = FLAG[[0x30FF + R2 + 1]] + (~[0x30E6 + 0x18 + (~[0x30FF + R2 + 2] + 1)] + 1) = FLAG[[0x30FF + R2 + 1]] - [0x30E6 + 0x18 + (~[0x30FF + R2 + 2] + 1)],flag密文比较
x306A 0000010111101010 x05EA BRZ x3055 ;二者相等则继续
x306B 0000111000000101 x0E05 BRNZP x3071 ;不相等说明flag不对,GOTO try again
x306C 0010000000001101 x200D LD R0, x307A ;换行
x306D 1111000000100001 xF021 TRAP OUT
x306E 1110000001000000 xE040 LEA R0, x30AF ;SUCCESS!
x306F 1111000000100010 xF022 TRAP PUTS
x3070 0000111000000101 x0E05 BRNZP x3076
x3071 0010000000001000 x2008 LD R0, x307A ;换行
x3072 1111000000100001 xF021 TRAP OUT
x3073 1110000001100101 xE065 LEA R0, x30D9 ;TRY AGAIN!
x3074 1111000000100010 xF022 TRAP PUTS
x3075 0000111000000000 x0E00 BRNZP x3076
x3076 1111000000100101 xF025 TRAP HALT
x3077 0000000000010001 x0011 NOP
x3078 0000000000010011 x0013 NOP
x3079 0000000000010100 x0014 NOP
x307A 0000000000001010 x000A NOP
x307B 0000000001010111 x0057 NOP ;W
x307C 0000000001100101 x0065 NOP ;e
x307D 0000000001101100 x006C NOP ;l
x307E 0000000001100011 x0063 NOP ;c
x307F 0000000001101111 x006F NOP ;o
x3080 0000000001101101 x006D NOP ;m
x3081 0000000001100101 x0065 NOP ;e
x3082 0000000000100000 x0020 NOP
x3083 0000000001110100 x0074 NOP
x3084 0000000001101111 x006F NOP
x3085 0000000000100000 x0020 NOP
x3086 0000000001110100 x0074 NOP
x3087 0000000001101000 x0068 NOP
x3088 0000000001100101 x0065 NOP
x3089 0000000000100000 x0020 NOP
x308A 0000000001110111 x0077 NOP
x308B 0000000001101111 x006F NOP
x308C 0000000001110010 x0072 NOP
x308D 0000000001101100 x006C NOP
x308E 0000000001100100 x0064 NOP
x308F 0000000000100000 x0020 NOP
x3090 0000000001101111 x006F NOP
x3091 0000000001100110 x0066 NOP
x3092 0000000000100000 x0020 NOP
x3093 0000000001001100 x004C NOP
x3094 0000000001000011 x0043 NOP
x3095 0000000000110011 x0033 NOP
x3096 0000000000000000 x0000 NOP
x3097 0000000001010000 x0050 NOP
x3098 0000000001101100 x006C NOP
x3099 0000000001100101 x0065 NOP
x309A 0000000001100001 x0061 NOP
x309B 0000000001110011 x0073 NOP
x309C 0000000001100101 x0065 NOP
x309D 0000000000100000 x0020 NOP
x309E 0000000001101001 x0069 NOP
x309F 0000000001101110 x006E NOP
x30A0 0000000001110101 x0075 NOP
x30A1 0000000001110000 x0070 NOP
x30A2 0000000001110100 x0074 NOP
x30A3 0000000000100000 x0020 NOP
x30A4 0000000001111001 x0079 NOP
x30A5 0000000001101111 x006F NOP
x30A6 0000000001110101 x0075 NOP
x30A7 0000000001110010 x0072 NOP
x30A8 0000000000100000 x0020 NOP
x30A9 0000000001100110 x0066 NOP
x30AA 0000000001101100 x006C NOP
x30AB 0000000001100001 x0061 NOP
x30AC 0000000001100111 x0067 NOP
x30AD 0000000000111010 x003A NOP
x30AE 0000000000000000 x0000 NOP
x30AF 0000000001010011 x0053 NOP
x30B0 0000000001110101 x0075 NOP
x30B1 0000000001100011 x0063 NOP
x30B2 0000000001100011 x0063 NOP
x30B3 0000000001100101 x0065 NOP
x30B4 0000000001110011 x0073 NOP
x30B5 0000000001110011 x0073 NOP
x30B6 0000000000100001 x0021 NOP
x30B7 0000000000100000 x0020 NOP
x30B8 0000000001011001 x0059 NOP
x30B9 0000000001101111 x006F NOP
x30BA 0000000001110101 x0075 NOP
x30BB 0000000001110010 x0072 NOP
x30BC 0000000000100000 x0020 NOP
x30BD 0000000001100110 x0066 NOP
x30BE 0000000001101100 x006C NOP
x30BF 0000000001100001 x0061 NOP
x30C0 0000000001100111 x0067 NOP
x30C1 0000000000100000 x0020 NOP
x30C2 0000000001101001 x0069 NOP
x30C3 0000000001110011 x0073 NOP
x30C4 0000000000100000 x0020 NOP
x30C5 0000000001111000 x0078 NOP
x30C6 0000000001101101 x006D NOP
x30C7 0000000001100011 x0063 NOP
x30C8 0000000001110100 x0074 NOP
x30C9 0000000001100110 x0066 NOP
x30CA 0000000001111011 x007B NOP
x30CB 0000000001111011 x007B NOP
x30CC 0000000001111001 x0079 NOP
x30CD 0000000001101111 x006F NOP
x30CE 0000000001110101 x0075 NOP
x30CF 0000000001110010 x0072 NOP
x30D0 0000000000100000 x0020 NOP
x30D1 0000000001101001 x0069 NOP
x30D2 0000000001101110 x006E NOP
x30D3 0000000001110000 x0070 NOP
x30D4 0000000001110101 x0075 NOP
x30D5 0000000001110100 x0074 NOP
x30D6 0000000001111101 x007D NOP
x30D7 0000000001111101 x007D NOP
x30D8 0000000000000000 x0000 NOP
x30D9 0000000001010100 x0054 NOP
x30DA 0000000001110010 x0072 NOP
x30DB 0000000001111001 x0079 NOP
x30DC 0000000000100000 x0020 NOP
x30DD 0000000001100001 x0061 NOP ;a
x30DE 0000000001100111 x0067 NOP ;g
x30DF 0000000001100001 x0061 NOP ;a
x30E0 0000000001101001 x0069 NOP ;i
x30E1 0000000001101110 x006E NOP ;n
x30E2 0000000000100001 x0021 NOP ;!
x30E3 0000000000000000 x0000 NOP
x30E4 0100000000000000 x4000 JSRR R0
x30E5 0000000000011000 x0018 NOP
x30E6 0000000001101100 x006C NOP
x30E7 0000000000001111 x000F NOP
x30E8 0000000001010000 x0050 NOP
x30E9 0000000001101100 x006C NOP
x30EA 0000000001101110 x006E NOP
x30EB 0000000001000010 x0042 NOP
x30EC 0000000000101100 x002C NOP
x30ED 0000000000101100 x002C NOP
x30EE 0000000000011110 x001E NOP
x30EF 0000000000001100 x000C NOP
x30F0 0000000000001101 x000D NOP
x30F1 0000000000000000 x0000 NOP
x30F2 0000000000110011 x0033 NOP
x30F3 0000000000111101 x003D NOP
x30F4 0000000000010111 x0017 NOP
x30F5 0000000000000001 x0001 NOP
x30F6 0000000000101011 x002B NOP
x30F7 0000000000111100 x003C NOP
x30F8 0000000000001100 x000C NOP
x30F9 0000000000000010 x0002 NOP
x30FA 0000000000011101 x001D NOP
x30FB 0000000000011100 x001C NOP
x30FC 0000000000001001 x0009 NOP
x30FD 0000000000010001 x0011 NOP
x30FE 0000000000010001 x0011 NOP
x30FF 0000000000010011 x0013 NOP
x3100 0000000000000001 x0001 NOP
x3101 0000000000000000 x0000 NOP
x3102 0000000000010100 x0014 NOP
x3103 0000000000000000 x0000 NOP
x3104 0000000000000000 x0000 NOP
x3105 0000000000010011 x0013 NOP
x3106 0000000000000010 x0002 NOP
x3107 0000000000000001 x0001 NOP
x3108 0000000000010100 x0014 NOP
x3109 0000000000000001 x0001 NOP
x310A 0000000000000001 x0001 NOP
x310B 0000000000010011 x0013 NOP
x310C 0000000000000011 x0003 NOP
x310D 0000000000000010 x0002 NOP
x310E 0000000000010100 x0014 NOP
x310F 0000000000000010 x0002 NOP
x3110 0000000000000010 x0002 NOP
x3111 0000000000010011 x0013 NOP
x3112 0000000000000100 x0004 NOP
x3113 0000000000000011 x0003 NOP
x3114 0000000000010100 x0014 NOP
x3115 0000000000000011 x0003 NOP
x3116 0000000000000011 x0003 NOP
x3117 0000000000010011 x0013 NOP
x3118 0000000000000101 x0005 NOP
x3119 0000000000000100 x0004 NOP
x311A 0000000000010100 x0014 NOP
x311B 0000000000000100 x0004 NOP
x311C 0000000000000100 x0004 NOP
x311D 0000000000010011 x0013 NOP
x311E 0000000000000110 x0006 NOP
x311F 0000000000000101 x0005 NOP
x3120 0000000000010100 x0014 NOP
x3121 0000000000000101 x0005 NOP
x3122 0000000000000101 x0005 NOP
x3123 0000000000010011 x0013 NOP
x3124 0000000000000111 x0007 NOP
x3125 0000000000000110 x0006 NOP
x3126 0000000000010100 x0014 NOP
x3127 0000000000000110 x0006 NOP
x3128 0000000000000110 x0006 NOP
x3129 0000000000010011 x0013 NOP
x312A 0000000000001000 x0008 NOP
x312B 0000000000000111 x0007 NOP
x312C 0000000000010100 x0014 NOP
x312D 0000000000000111 x0007 NOP
x312E 0000000000000111 x0007 NOP
x312F 0000000000010011 x0013 NOP
x3130 0000000000001001 x0009 NOP
x3131 0000000000001000 x0008 NOP
x3132 0000000000010100 x0014 NOP
x3133 0000000000001000 x0008 NOP
x3134 0000000000001000 x0008 NOP
x3135 0000000000010011 x0013 NOP
x3136 0000000000001010 x000A NOP
x3137 0000000000001001 x0009 NOP
x3138 0000000000010100 x0014 NOP
x3139 0000000000001001 x0009 NOP
x313A 0000000000001001 x0009 NOP
x313B 0000000000010011 x0013 NOP
x313C 0000000000001011 x000B NOP
x313D 0000000000001010 x000A NOP
x313E 0000000000010100 x0014 NOP
x313F 0000000000001010 x000A NOP
x3140 0000000000001010 x000A NOP
x3141 0000000000010011 x0013 NOP
x3142 0000000000001100 x000C NOP
x3143 0000000000001011 x000B NOP
x3144 0000000000010100 x0014 NOP
x3145 0000000000001011 x000B NOP
x3146 0000000000001011 x000B NOP
x3147 0000000000010011 x0013 NOP
x3148 0000000000001101 x000D NOP
x3149 0000000000001100 x000C NOP
x314A 0000000000010100 x0014 NOP
x314B 0000000000001100 x000C NOP
x314C 0000000000001100 x000C NOP
x314D 0000000000010011 x0013 NOP
x314E 0000000000001110 x000E NOP
x314F 0000000000001101 x000D NOP
x3150 0000000000010100 x0014 NOP
x3151 0000000000001101 x000D NOP
x3152 0000000000001101 x000D NOP
x3153 0000000000010011 x0013 NOP
x3154 0000000000001111 x000F NOP
x3155 0000000000001110 x000E NOP
x3156 0000000000010100 x0014 NOP
x3157 0000000000001110 x000E NOP
x3158 0000000000001110 x000E NOP
x3159 0000000000010011 x0013 NOP
x315A 0000000000010000 x0010 NOP
x315B 0000000000001111 x000F NOP
x315C 0000000000010100 x0014 NOP
x315D 0000000000001111 x000F NOP
x315E 0000000000001111 x000F NOP
x315F 0000000000010011 x0013 NOP
x3160 0000000000010001 x0011 NOP
x3161 0000000000010000 x0010 NOP
x3162 0000000000010100 x0014 NOP
x3163 0000000000010000 x0010 NOP
x3164 0000000000010000 x0010 NOP
x3165 0000000000010011 x0013 NOP
x3166 0000000000010010 x0012 NOP
x3167 0000000000010001 x0011 NOP
x3168 0000000000010100 x0014 NOP
x3169 0000000000010001 x0011 NOP
x316A 0000000000010001 x0011 NOP
x316B 0000000000010011 x0013 NOP
x316C 0000000000010011 x0013 NOP
x316D 0000000000010010 x0012 NOP
x316E 0000000000010100 x0014 NOP
x316F 0000000000010010 x0012 NOP
x3170 0000000000010010 x0012 NOP
x3171 0000000000010011 x0013 NOP
x3172 0000000000010100 x0014 NOP
x3173 0000000000010011 x0013 NOP
x3174 0000000000010100 x0014 NOP
x3175 0000000000010011 x0013 NOP
x3176 0000000000010011 x0013 NOP
x3177 0000000000010011 x0013 NOP
x3178 0000000000010101 x0015 NOP
x3179 0000000000010100 x0014 NOP
x317A 0000000000010100 x0014 NOP
x317B 0000000000010100 x0014 NOP
x317C 0000000000010100 x0014 NOP
x317D 0000000000010011 x0013 NOP
x317E 0000000000010110 x0016 NOP
x317F 0000000000010101 x0015 NOP
x3180 0000000000010100 x0014 NOP
x3181 0000000000010101 x0015 NOP
x3182 0000000000010101 x0015 NOP
x3183 0000000000010011 x0013 NOP
x3184 0000000000010111 x0017 NOP
x3185 0000000000010110 x0016 NOP
x3186 0000000000010100 x0014 NOP
x3187 0000000000010110 x0016 NOP
x3188 0000000000010110 x0016 NOP
x3189 0000000000010011 x0013 NOP
x318A 0000000000011000 x0018 NOP
x318B 0000000000010111 x0017 NOP
x318C 0000000000010100 x0014 NOP
x318D 0000000000010111 x0017 NOP
x318E 0000000000010111 x0017 NOP
x318F 0000000000010100 x0014 NOP
x3190 0000000000011000 x0018 NOP
x3191 0000000000011000 x0018 NOP
x3192 0000000000000000 x0000 NOP
x3193 0000000000000000 x0000 NOP
x3194 0000000000000000 x0000 NOP
x3195 0000000000000000 x0000 NOP
x3196 0000000000000000 x0000 NOP
x3197 0000000000000000 x0000 NOP
x3198 0000000000000000 x0000 NOP
x3199 0000000000000000 x0000 NOP
x319A 0000000000000000 x0000 NOP
x319B 0000000000000000 x0000 NOP
x319C 0000000000000000 x0000 NOP
x319D 0000000000000000 x0000 NOP
x319E 0000000000000000 x0000 NOP
x319F 0000000000000000 x0000 NOP
|