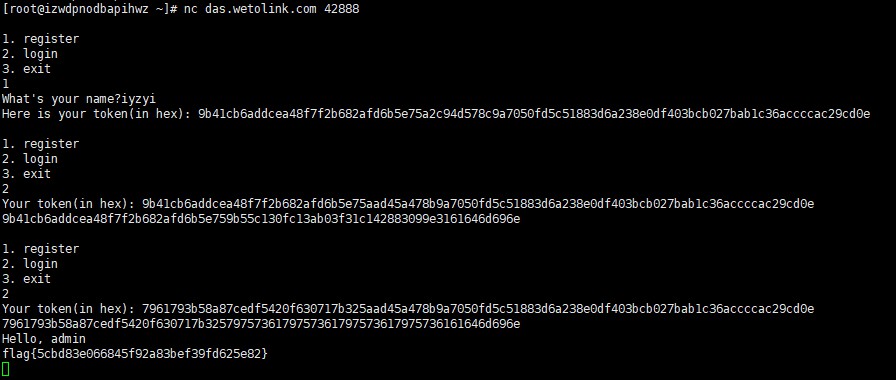
中午才起床,舍友喊我起床恰烂钱。ak了密码。逆向只做了了一题。没时间了。不到五小时做了500分我个人感jio还行吧。
crypto
rsa
1 | ('c=', '0x7a7e031f14f6b6c3292d11a41161d2491ce8bcdc67ef1baa9eL') |
入门难度,通过给出表达式轻松求出p和q
1 | from Crypto.Util.number import * |
Yusa_cbc
1 | from Crypto.Cipher import AES |
cbc bit flipping攻击
两个密文块,通过改第一个密文块,可以使得第二个密文块解密出admin.
但是这会使得第一个密文块解密出乱码。而题目也需要第一个密文块的值为yusayusayusayusa.
好在题目给出了三次交互的机会,第一次用于登陆,第二次用于改第一个密文块,从而使第二个密文块解密出admin。
第三次交互,需要从第二次交互的输出中提取第一个密文块的明文,与yusayusayusayusa异或后,再与iv进行异或,作为新的iv。这样aes cbc解密出乱码也没关系,因为会被iv抵消掉乱码。
1 | from binascii import * |
Yusa_ecb
1 | from Crypto.Cipher import AES |
byte at a time 攻击。
首先通过更改plaintext的长度,测出flag长度是38(plaintext长为10的时候,密文长度48,长为11的时候,密文长度64)
参考了这篇文章:ECB Byte at Time - scriptkid - 博客园 (cnblogs.com)
每次爆破一个字符即可。
1 | from pwn import * |
逆向
RealEzRE
这题很有意思。
字符串都是加密过的了,走了一个类似base64的解码。
有两个反调试,一个是时间调试,另一个我没深入去看:
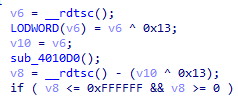
看了看,跟进这个函数:
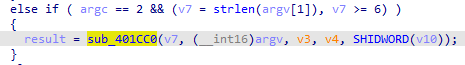
里面是个smc,但我没找到具体的smc的解码代码。
索性直接解码后dump出来。虽然不能动调了,但是可以静态看。
1 | dword_437FA0 = 825373492; |
稍微看了下,就一个rc4,没别的了。
解密脚本:
1 | from Crypto.Cipher import ARC4 |